Over the years, blockchain technology has led to several applications. Cryptocurrency has been a hot topic since 2016 and now NFTs are dominating the news. DAO, or Decentralized Autonomous Organization, is another blockchain application that could take center stage.
But, What is DAO?
DAO or Decentralized Autonomous organizations are decentralized venture funds that operate through smart contracts. Here the financial transactions and rules are encoded on a blockchain, removing the need for a central governing authority.
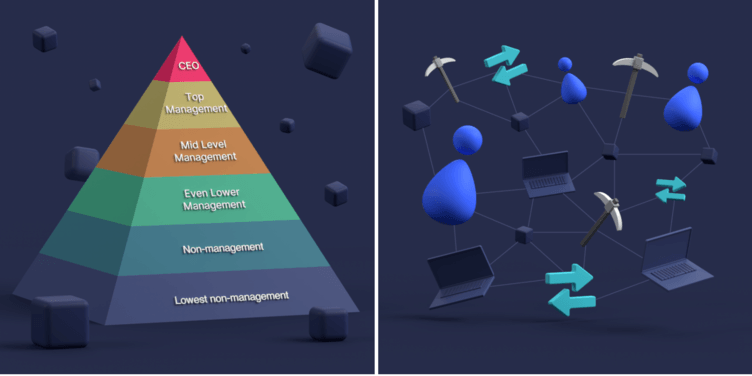
Contrary to the centralized venture DAO doesn’t have a hierarchy system. It doesn’t rely on the CEO to pass orders down the line, but smart contracts to complete actions.
A Creative Start for DAO
The idea of DAO was first conceptualized in 2015 by a team called Slock.It. Ethereum was conceived by Vitalik Buterin just a few months ago.
Ethereum was still in its infant stage. In May 2016, “The DAO” was launched and it became a hot topic within a few days. The concept was new, creative and people were excited.
The DAO had a creation period during which people could exchange Ether with DAO tokens. People were receiving 100 DAO tokens with 1 Ether.
The creation period was a massive success as the platform collected 12.7 Ether, making it the biggest crowdfund ever.
The decentralized platform would allow anyone to pitch their idea to the community to receive funding. Anyone having DAO tokens could vote on those ideas and could receive rewards if the projects turned into a profit. With such a structure in place, everything was looking great.
The Hacking Incident No one Expected
It was June 17, when a hacker found a loophole in the coding. The hacker exploited the opportunity to drain funds from the DAO. The miscreants stole about 3.6 million ETH, the equivalent of $70 million at the time within a few hours. The hacker withdrew the attack once he had done the intended damage.
The incident made one thing clear that the code written for The DAO had multiple flaws, and repetitive exploitation was one of them. Another way to look at this situation is by an example.
Imagine you withdraw $100 from an ATM. You get $100, but the balance didn’t show any change. To check again you go ahead and withdraw another $100. Yet again, NO CHANGE!
You keep going on as you withdraw more until you have withdrawn cash which is more than your total balance in your account. You keep going on until finally, your balance reflects on the screen -$100,000, or $0 in the ideal case — yet you only had a total initial balance of $1,000.
Now you have $100000 in your hand which is much more than your initial balance of $1000. What happened is that the ATM kept withdrawing from your original balance without updating the previous transactions.
The ATM saw your original $1000 balance every time you withdrew $100. It never updated to $900. You ran the ATM in a loop to withdraw from the initial $1000 indefinitely. This is what happened during “The DAO” hack.
The Inbuilt Malicious Application
There was an application built on Ethereum which emulated action similar to the ATM example above. This allowed the hackers to drain funds above the allowed allocation. The hacker continuously executed withdrawals before the balance was updated.
However, the developers placed the funds into an account subject to a 28-day holding period so that the hacker couldn’t get away. To refund the lost money, Ethereum hard forked to send the hacked funds to an account available to the original owners.
Post the attack on DAO there were some serious implications as crypto exchange Kraken and Poloniex delisted the DAO token. Furthermore, according to the United States Securities and Exchange Commission (SEC), The DAO violated federal securities laws, along with all of its investors.
The Aftermath
The whole incident teaches a valuable incident about the importance of establishing secure blockchain platforms. The DAO’s hack happened due to the presence of a coding loophole.
The aftermath of the SEC’s ruling on The DAO encouraged blockchain startups to look for ways to avoid security registration and federal regulation.
Five years after the incident, billions and billions of dollars reside in multiple smart contracts across the Ethereum ecosystem. According to Defi Pulse, the top three projects are Maker, AAVE, and Compound — which combine to hold ~$26.5 billion worth of Ethereum.
We can say that these early failures were crucial in setting up a healthy ecosystem in the long term, which now appears to be thriving.
The Possible Future for DAO
In the future, people’s income will be a mix of things – be it something we do for entertainment (e.g., play games), be it some kind of traditional work (e.g., bounties/contracts), and also the things that cover a small percentage of the population (e.g., investing, passive income).
For example, a token holder may earn a part of his income from receiving grants to major Defi protocols (e.g., Compound), from passive yield income on their tokens, and some through returns as their ownership stakes grow with time. On the other hand, a bounty hunter will earn by completing incentivized on-chain actions; a network participant may earn from playing games like Axie Infinity or other “play-to-earn” games that will come up.
In this new future of work, opportunities will be more visible, switching costs between jobs will be lower. Further, work will be reduced down into more atomic units, and the entire world will be unified under a single workforce with access to all opportunities. We will witness new opportunities based on our on-chain history, ownership, and reputation, and we will be matched to contribute where we have the best advantage.
The older way to earn was “work-to-earn,” but the future of income is “x-to-earn” — play to earn, learn to earn, create to learn, and work to earn.
